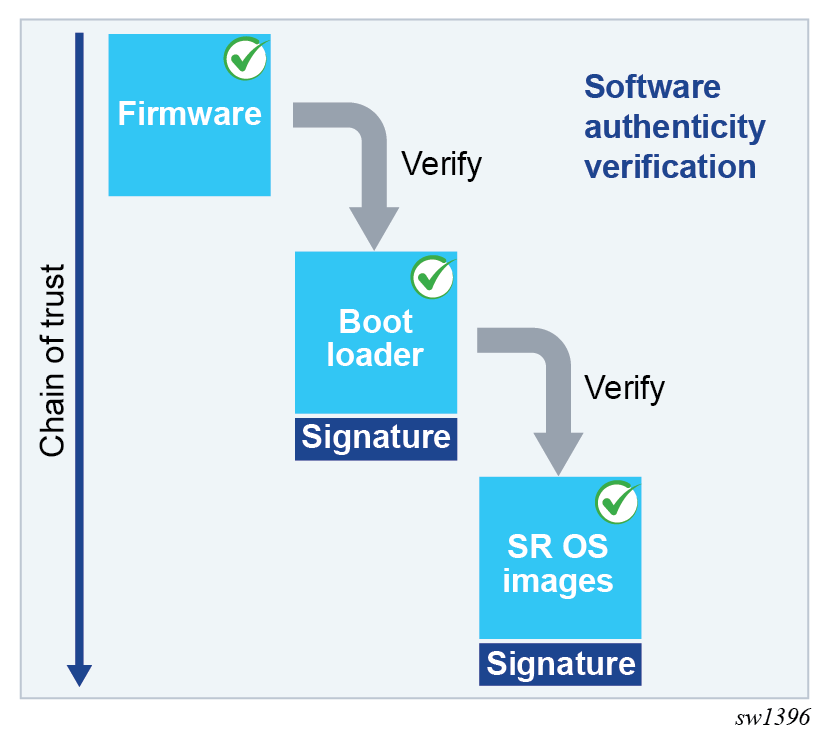
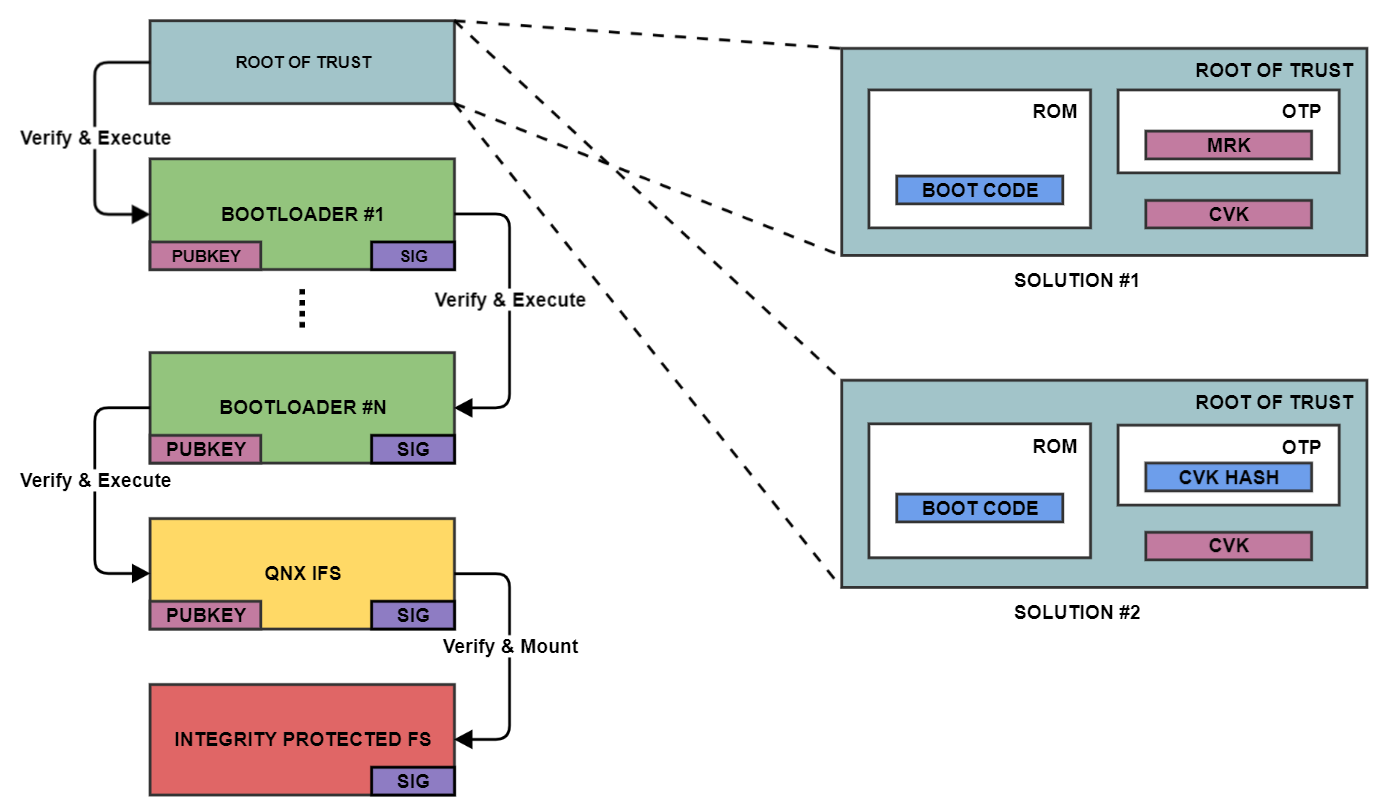
Overview of the Trusted/Verified Boot implementation according to the... | Download Scientific Diagram

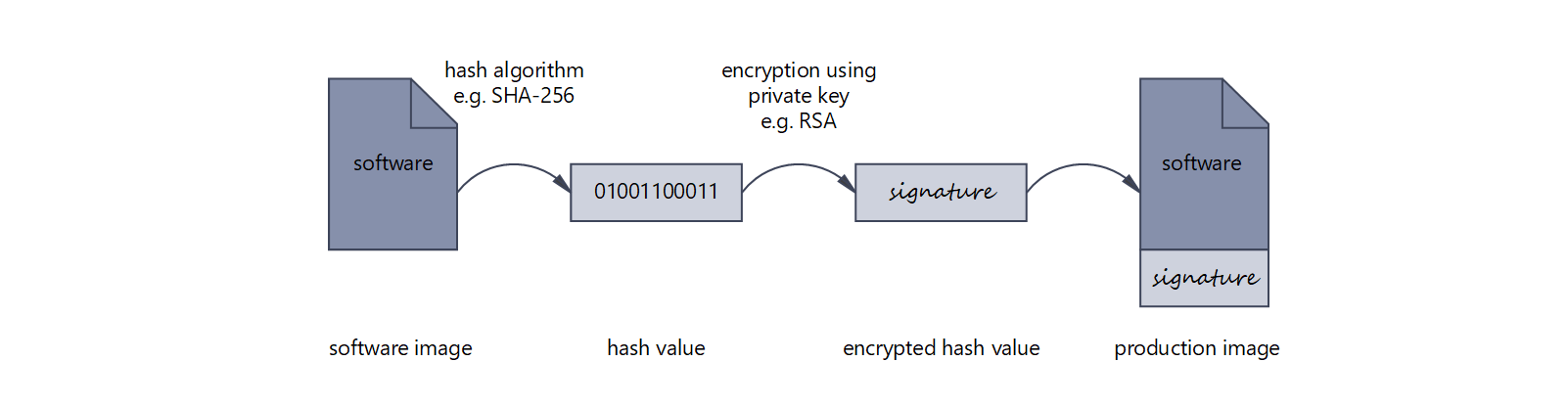
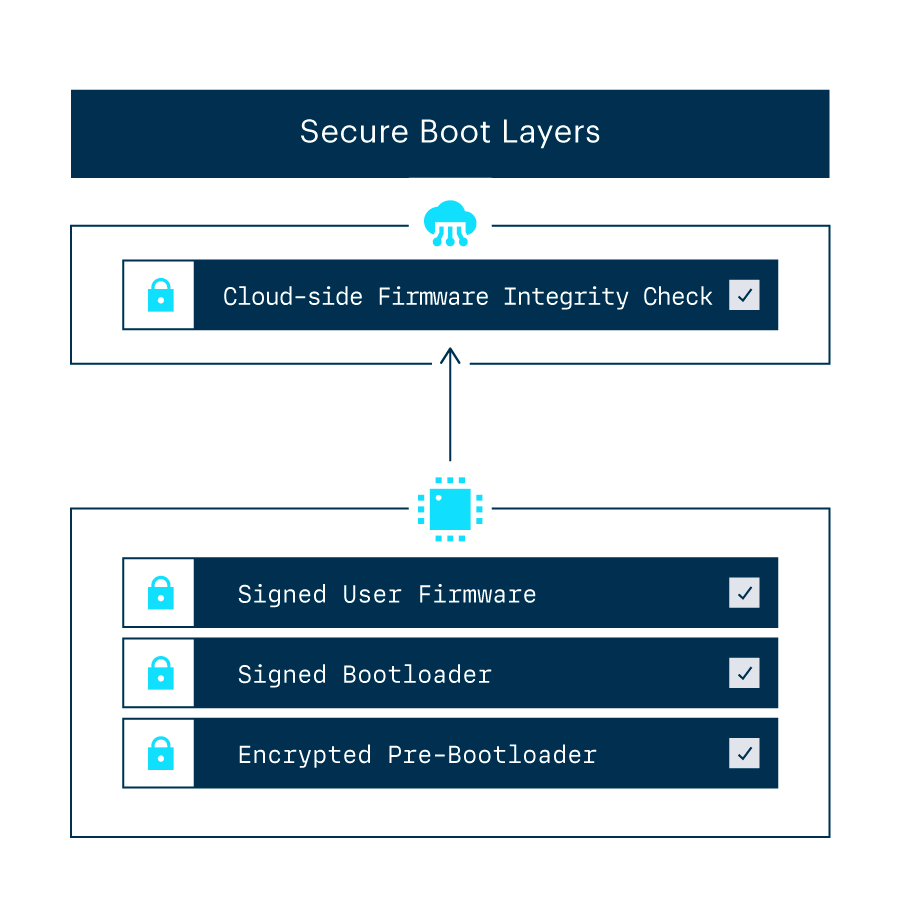
Build highly secure IOT device: secure boot, measured boot and attestation, secure storage etc | by lei zhou | Medium

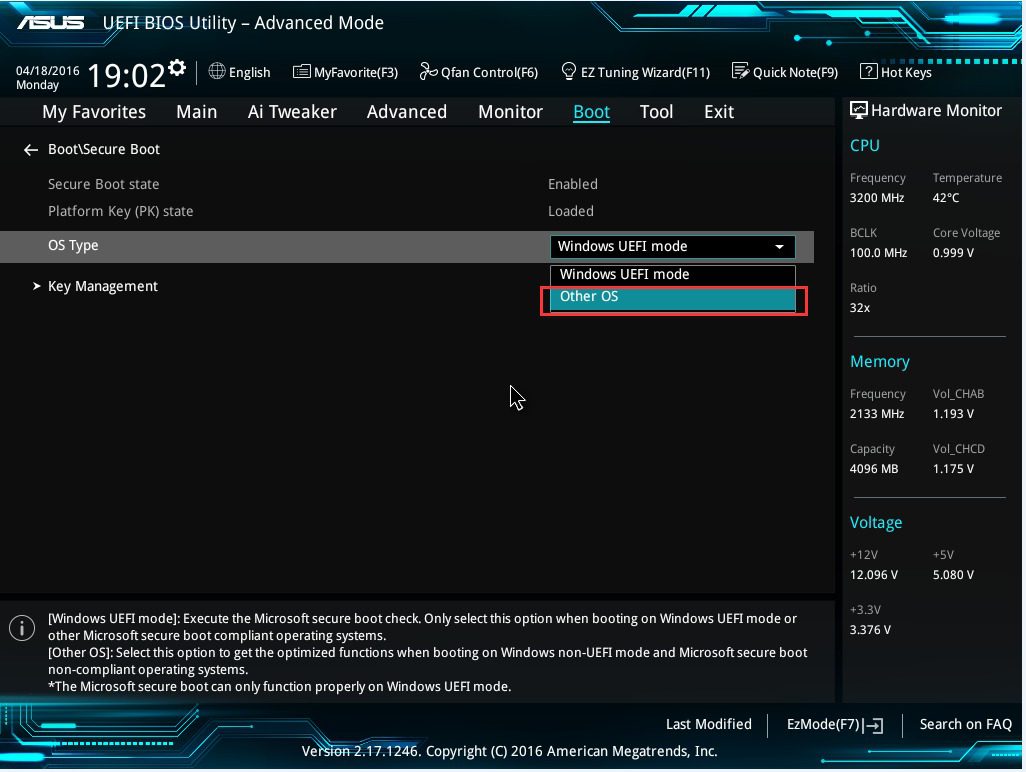
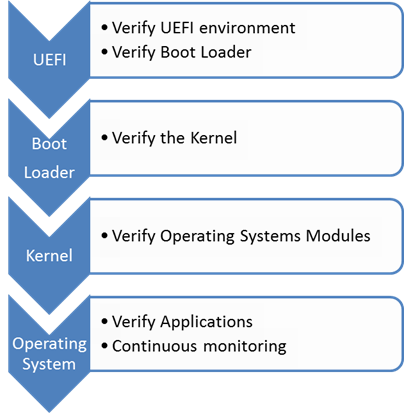
SOLVED: SECURE BOOT vs TRUSTED BOOT vs MEASURED BOOT, Whats the Difference? | Up & Running Technologies, Tech How To's

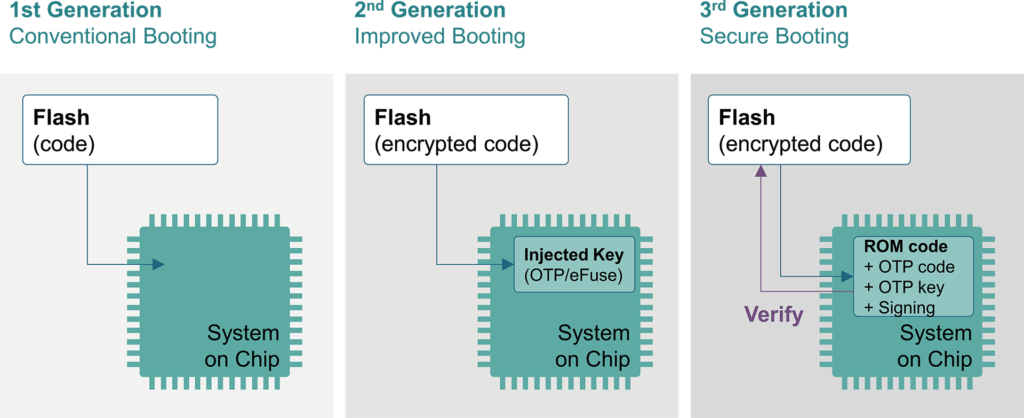
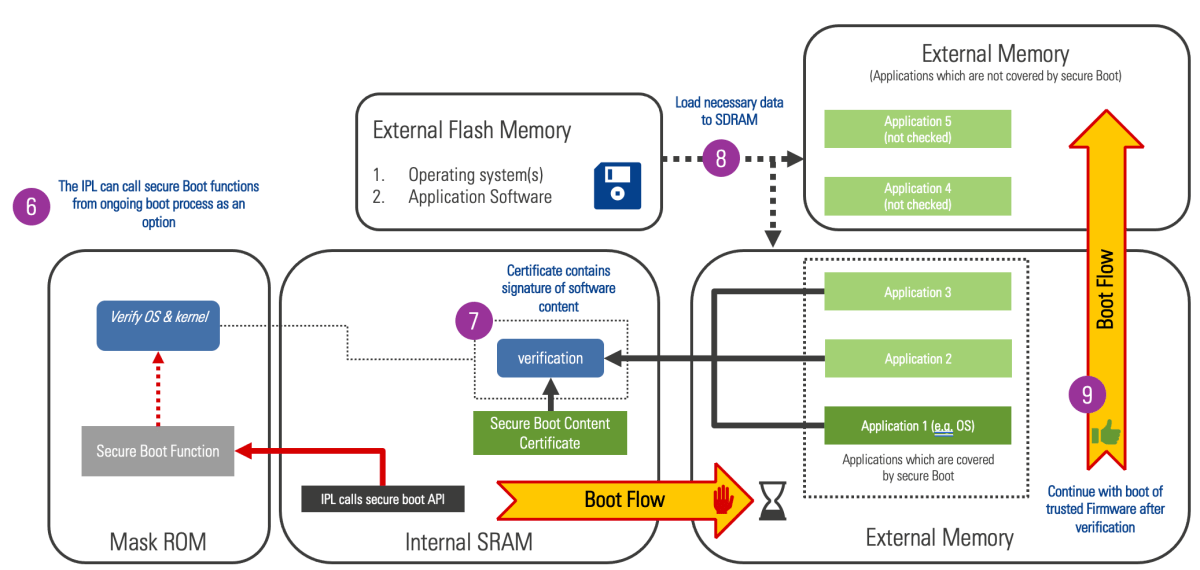
Common structure of secure processors processor, securing an embedded... | Download Scientific Diagram